 Sabtu, 11 Januari 2025 (09:59)
Sabtu, 11 Januari 2025 (09:59)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
Taking over a website with JWT Tokens! (Tech Raj) View |
 |
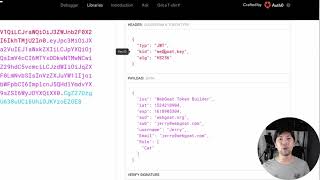
What Is JWT and Why Should You Use JWT (Web Dev Simplified) View |
 |
JSON Web Token Hacking (Loi Liang Yang) View |
 |
Understanding JSON Web Tokens | JWT Explanation from Tech with Tim (Akamai Developer) View |
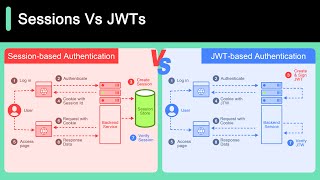 |
Session Vs JWT: The Differences You May Not Know! (ByteByteGo) View |
 |
BUG BOUNTY TUTORIAL: ACCOUNT TAKEOVER | JWT HACKING (BePractical) View |
 |
Cracking JSON Web Tokens (The Cyber Mentor) View |
 |
JWT | JSON Web Token | Bug Bounty | Penetration Testing (Ryan John) View |
 |
How Does JWT Authentication Work (JSON Web Token) | Tokens vs Sessions (Nikita Dev) View |
 |
JWT Vulnerabilities! 🔒 (VatsalSecurity) View |