 Sabtu, 28 Desember 2024 (00:02)
Sabtu, 28 Desember 2024 (00:02)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
How Lockheed's Cyber Kill Chain Maps Cyber Attacks EASILY (StudioSec) View |
 |
Breaking The Kill Chain: A Defensive Approach (The CISO Perspective) View |
 |
Real Hacking: Learn The Cyber Kill Chain (Cyberspatial) View |
 |
The Cyber Kill Chain (Sunny Classroom) View |
 |
Lockheed Martin Cyber Kill Chain | The Defender's Mini Playbook (Jason Rebholz - TeachMeCyber) View |
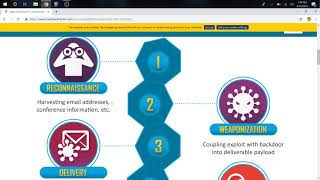 |
THE CYBER KILL CHAIN | HOW HACKERS DO WHAT THEY DO (BitByte) View |
 |
Cyber Kill Chain u0026 Defenses (Sekaurity) View |
 |
CompTIA CySA+ Full Course Part 09: Attack Frameworks and The Cyber Kill Chain (Certify Breakfast) View |
 |
Cyber Threat Intelligence Lab 4 Cyber Kill Chain, Pyramid of Pain, Diamond Model (Level Effect) View |
 |
Overview of Cyber Kill Chain Framework (CyberMentor) View |